Definition
Key Concepts
Level
Reference
Anti Money Laundering (AML)
Anti-money laundering (AML) refers to the laws, regulations and procedures intended to prevent criminals from disguising illegally obtained funds as legitimate income. Though anti-money laundering laws cover a limited range of transactions and criminal behavior, their implications are far-reaching. For example, AML regulations require banks and other financial institutions that issue credit or accept customer deposits to follow rules that ensure they are not aiding money-laundering.
Anti -laundering (AML) refers to the activities intended to prevent individuals from transferring value obtained illegally into a legitimate sources of income.
- AML regulations require financial institutions to monitor customers' transactions and report on suspicious financial activity.
Anti Money Laundering (AML) seeks to deter criminals by making it harder for them to hide ill-gotten money.
Criminals use money laundering to conceal their crimes and the money derived from them.
AML regulations require financial institutions to monitor customers' transactions and report on suspicious financial activity.
Application
"A blockchain is a peer-to-peer distributed ledger forged by consensus, combined with a system for "smart contracts" and other assistive technologies". hyperledger.org
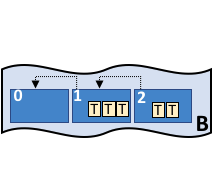
A blockchain is a chain of blocks each containing transaction (transition) data. Each block, except the first block, is linked with the previous block together forming a chain. Once a block has entered the blockchain, it can not be altered resulting in data immutability .
A blockchain is a continuously growing list of records, which are ordered and combined/grouped into blocks. Such blocks are linked (or "chained") using cryptography. The first block in a blockchain is called the genesis block, and each following block is appended after the last block in the chain.
Each block typically contains a cryptographic hash of the previous block. Since each new block contains a hash of the previous block, a blockchain is inherently resistant to modification of historical data. In typical blockchain implementations, the records that are grouped into a block are referred to as transactions that take place between parties and are added to the about-to-be-written block after they have been verified.
For use as a distributed ledger, a blockchain is typically managed by a peer-to-peer network collectively adhering to a protocol for validating new blocks. Once recorded, the data in any given block cannot be altered retroactively without the alteration of all subsequent blocks, which requires collusion of the network majority.
Money laundering is the illegal process of making "dirty" money appear legitimate instead of ill-gotten.
Criminals use a wide variety of money laundering techniques to make illegally obtained funds appear clean.
Online banking and cryptocurrencies have made it easier for criminals to transfer and withdraw money without detection.
The prevention of money laundering has become an international effort and now includes terrorist funding among its targets.



https://www.investopedia.com/terms/m/moneylaundering.asp
LFS272
Byzantine Fault Tolerant Consensus
Byzantine Fault Tolerance (BFT) is defined as the feature of a distributed network to reach consensus (agreement on the same value) even when some of the nodes in the network fail to respond or respond with incorrect information.
An important consideration to be aware of while setting up a blockchain network is the requirements of Byzantine Fault Tolerant (BFT) consensus, compared with the Crash Fault Tolerant (CFT) one. Due to the underlying complexity of BFT consensus algorithms, a best practice is for the community to leverage the latest academically-proven consensus algorithms based on rigorous and peer-reviewed demonstrations of the safety and liveness properties. Such algorithms include the Tendermint, Algorand, Mir-BFT and HotStuff. There is also some on-going work on Golang-based implementation of the BFT-SMART algorithm for Hyperledger Fabric. These are important reference points for blockchain architects and developers interested in adopting BFT consensus in the future. At Oracle ,we are actively exploring the available options to ensure they meet the rigorous proof requirements as well as deliver operational characteristics, including performance and resilience required in enterprise applications.
Certificate Authority
In cryptography, a certificate authority or certification authority (CA) is an entity that issues digital certificates. A digital certificate certifies the ownership of a public key by the named subject of the certificate. This allows others (relying parties) to rely upon signatures or on assertions made about the private key that corresponds to the certified public key. A CA acts as a trusted third party—trusted both by the subject (owner) of the certificate and by the party relying upon the certificate. Wikipedia
The Certificate Authority (CA) provides a number of certificate services to users of a blockchain. More specifically, these services relate to user enrollment, transactions invoked on the blockchain, and TLS -secured connections between users or components of the blockchain. This guide builds on either the fabric developer’s setup or the prerequisites articulated in the fabric network setup guide.
Chaincode - Smart contracts in Hyperledger Fabric. A smart contract defines the executable logic that generates new facts that are added to the ledger. A chaincode is typically used by administrators to group related smart contracts for deployment, but can also be used for low level system programming of Fabric,.
that manages access and modifications to a set of key-value pairs in the World State via Transaction. In Hyperledger Fabric, smart contracts are packaged as chaincode. Chaincode is installed on peers and then defined and used on one or more channels.
A chaincode definition is used by organizations to agree on the parameters of a chaincode before it can be used on a channel. Each channel member that wants to use the chaincode to endorse transactions or query the ledger needs to approve a chaincode definition for their organization. Once enough channel members have approved a chaincode definition to meet the Lifecycle Endorsement policy (which is set to a majority of organizations in the channel by default), the chaincode definition can be committed to the channel. After the definition is committed, the first invoke of the chaincode (or, if requested, the execution of the Init function) will start the chaincode on the channel.
A broader term overarching the entire transactional flow, which serves to generate an agreement on the order and to confirm the correctness of the set of transactions constituting a block.
- Coming to an agreement: The mechanism gathers all the agreements from the group as much as it can.
- Collaboration: Every one of the group aims toward a better agreement that results in the groups’ interests as a whole.
- Co-operation: Every individual will work as a team and put their own interests aside.
ERC20 Standards Token is the Ethereum token system ,which is used for Ethereum smart contracts platform. Developed in 2015, ERC-20 defines a common list of rules to function within the Ethereum ecosystem.
The Ethereum community created these standards with six mandatory and three optional rules.
Mandatory
- totalSupply
- balanceOf
- transfer
- transferFrom
- approve
- allowance
Optional
- Token Name
- Symbol
- Decimal (up to 18)
Other ERC Token standards for Ref.
- ERC-20 Token Standard. https://eips.ethereum.org/EIPS/eip-20
- ERC-165 Standard Interface Detection. https://eips.ethereum.org/EIPS/eip-165
- ERC-173 Owned Standard. https://eips.ethereum.org/EIPS/eip-173
- ERC-223 Token Standard. https://github.com/ethereum/EIPs/issues/223
- ERC-677
transferAndCallToken Standard. https://github.com/ethereum/EIPs/issues/677 ERC-721 Non-Fungible Token Standard https://eips.ethereum.org/EIPS/eip-721
- ERC-827 Token Standard. https://eips.ethereum.org/EIPS/eip-827
- ERC-1155 Multi-Token Standard https://eips.ethereum.org/EIPS/eip-1155
Digital government is the state-of-art concept from public administration science, a successor of e-government paradigm. The former model simply indicated the digitalisation of the public administration.
Digital government refers to the creation of new public services and service delivery models that leverage digital technologies and governmental and citizen information assets. The new paradigm focuses on the provision of user-centric , agile and innovative public services. Blockchain absolutely is the one of the most innovative digital technologies that has to be considered under the new paradigm of governmental policy making and service delivery.
A decentralized identifier (DID) is a pseudo-anonymous identifier for a person, company, object, etc. Each DID is secured by a private key. Only the private key owner can prove that they own or control their identity. One person can have many DIDs, which limits the extent to which they can be tracked across the multiple activities in their life. For example, a person could have one DID associated with a gaming platform, and another, entirely separate DID associated with their credit reporting platform.
In one example, users sign up to a self-sovereign identity and data platform to create and register a DID. During this process, the user creates a pair of private and public keys. Public keys associated to a DID can be stored on-chain in case keys are compromised or are rotated for security reasons. Additional data associated with a DID such as attestations can be anchored on-chain, but the full data itself should not be stored on-chain to maintain scalability and compliance with privacy regulations.
A decentralized identifier (DID) is a pseudo-anonymous identifier for a person, company, object, etc. Each DID is secured by a private key. Only the private key owner can prove that they own or control their identity. One person can have many DIDs, which limits the extent to which they can be tracked across the multiple activities in their life. For example, a person could have one DID associated with a gaming platform, and another, entirely separate DID associated with their credit reporting platform.
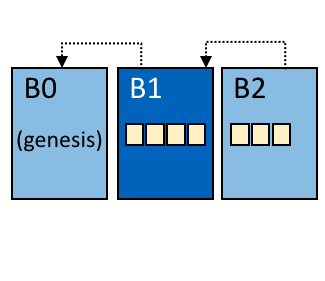
The Genesis Block is the first block or block zero in any blockchain-based system, It is the prototype of all other blocks in the blockchain network. Based on this which additional blocks are added to form a chain of blocks, hence we call them blockchain. In theory, there is no real need for a Genesis Block. However, it is necessary to have a starting point that everyone can trust.
The hash of genesis block is added to all new transactions in a new block. This combination is used to create its unique hash. This process is repeated until all the new blocks are added to a blockchain. Without Genesis Block, it would be really difficult for the participant to trust a blockchain and to know how and when it started.
Note : Every block in a blockchain stores a reference to the previous block. In the case of Genesis Block, there is no previous block for reference.
Technically it means that the Genesis Block has it’s “previous hash” value set to 0. Which means that no data was processed before the Genesis Block.All other blocks will have sequential numbers starting by 1, and will have a “previous hash” set to the hash of the previous block.
Proof of Stake (PoS) is a class of consensus algorithm that selects and rewards validators as a function of a validator’s economic stake in the network. Unlike PoW, the probability of creating a block in a PoS network is not a result of hash power from burning energy, but rather the result of economic value-at-loss. Proof of Stake will be the consensus mechanism that Ethereum 2.0 uses to maintain the network. Unlike Proof of Work networks, Proof of Stake networks can achieve finality. (consensys)
Proof of Work (PoW) is a class of consensus algorithm that rewards miners who expend computational energy to solve mathematical problems to propose new blocks. With PoW, the probability of mining a block and thus receiving block rewards is a function of how much computational energy (known as hash power) a miner expends. Popular blockchains such as Bitcoin, Ethereum (1.0), and Litecoin are all Proof of Work blockchains. ( consensys)
What is Stablecoins and how many and how they work?
The way Stablecoins achieves by collateralizing other real-world assets and pairing the value to them. As such, the value of stablecoins should never exceed the collateral in reserve, and therefore can (in most cases) be exchanged to the assets they’re pegged to at any time.
It's important to know that staple coins or non-mined ones and non pre-mined Instead, their total supply is always changing and reacting to the movements in the market. In order to control inflation, coins are burned when exchanged to the pegged asset. Likewise, when an asset is collateralized, newly created stablecoins enter the market.
Several different types of stablecoins currently exist. Even though the underlying principle is the same, the main difference is how a particular stablecoin maintains its value.
1, FIAT- backed Stable Coins , ex : USD $$
2, Commodity backed Stable coins , ex : GOLD
3, Cryptocurrency-backed stable coins, ex: bitcoin/eththereum
4, Seigniorage/Algo backed Stable coins , ex, : no proven example.
Ref : https://blog.knowledgesociety.tech/what-is-stablecoins-and-how-do-they-work/
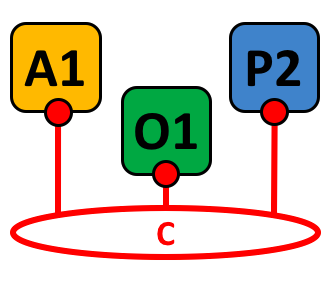
claims made by an issuer. A
Verifiable Credential is a
tamper-evident Credential that has
authorship that can be
W3C Verifiable Claims Working Group cryptographically verified.



hey I'm thinking we should either move this to the marketing part of the wiki or give it to the Learning materials group. Ry Jones what do you think?
Ry Jones
probably the latter - if they want it. If LMG doesn't want to maintain it, then marketing